This blog discusses the protocols used in the application layer of the OSI model. It contains all of the protocols' information. However, let's first examine what the OSI model entails.
The OSI Model: What Is It?
The seven levels that computer systems employ to interact over a network are described by the Open Systems Interconnection (OSI) model. Early in the 1980s, all significant computer and telecommunications businesses accepted it as the first industry standard for network communications.
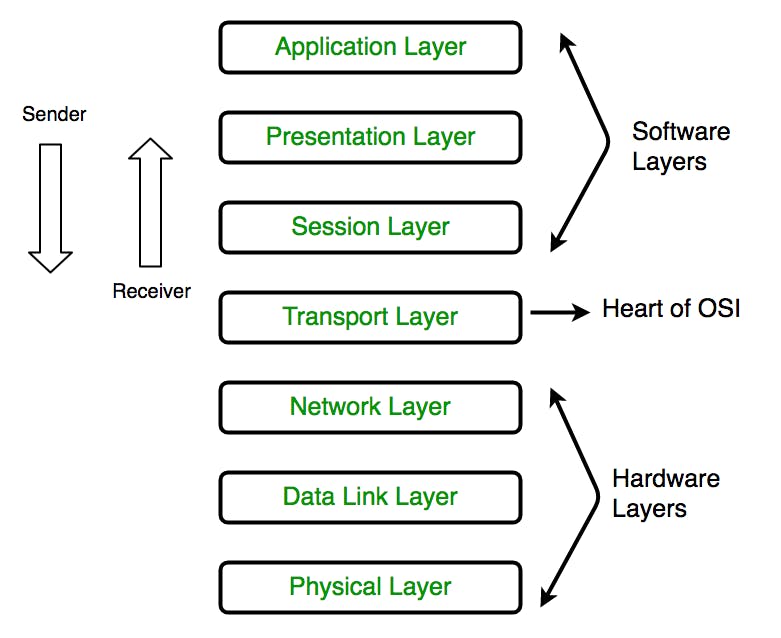
The simplified TCP/IP model, rather than OSI, is the foundation of the current Internet. The OSI 7-layer model is still extensively used, nevertheless, since it aids in both isolating and troubleshooting networking issues as well as helping to depict and convey how networks function.
The seventh layer of the OSI Model
The Application layer, which is implemented by network applications, is at the very top of the OSI Reference Model's stack of layers. These apps generate the data, which must be networked and transmitted. This layer also acts as a portal for application services to connect to the network and show the user the information they have received.
Applications- such as browsers and Skype Messenger, are one of the examples.

The OSI model's seventh and final layer is the application layer. This layer, known as the abstraction layer, uses the OSI and TCP/IP models to manage the sharing protocols over a computer network. The application layer of the internet protocol suite comprises the interface techniques and communication protocols used for network-based process-to-process communication. Several protocols are included at the application layer, including Telnet, FTP, TFTP, SMTP, SNMP, DNS, and DHCP.
Application layer protocol
The list of application layer protocols is shown below.
Telnet
- An application protocol is telnet. It offers a text-focused, interactive, bidirectional communication capability.
- Telnet employs terminal connections for text-based communication. Telnet may be used to configure many networking hardware components.
- An 8-bit byte-oriented data connection at TCP uses information that is interleaved in-band with Telnet control information.
- The client-server protocol known as Telnet is used to access the command line on distant computers.
Command:
telnet [\\RemoteServer] \\RemoteServer : Specifies the name of the server to which you want to connectFTP
- File Transfer Protocol is referred to as FTP. It is an application layer protocol that is used to move files across hosts, or from one place to another.
- It is a common method that TCP/IP offers.
- Although moving files across systems appears to be fairly straightforward, there are certain issues that must be resolved beforehand.
- TCP services are employed. Two TCP connections are required.
- A control connection and a data connection, respectively.
- It employs the well-known ports 21 and 20 for control and data connections, respectively.
Command:
ftp machinename
TFTP
- Trivial File Transfer Protocol (TFTP), also known as an application layer protocol, is used to deliver files from the server to the client.
- The UDP protocol is used by the trivial file transfer protocol to transfer files from server to client. UDP, or User Datagram Protocol, is used here.
- It is typically used to transfer data between computers that are only connected to the local network.
- The fact that trivial file transfer protocol consume less memory is its key strength. If computers lack hard drives, this application layer protocol might be used to transmit boot files.
- The port used for communication can be specified when Trivial File Transfer Protocol is set up, however it typically uses protocol 69.
Command:
tftp [ options... ] [host [port]] [-c command]
4 . SMTP
- SMTP is short for The emails are transferred using a straightforward mail transfer protocol.
- It outlines the requirements for sending back and forth between instructions and answers.
It is used twice: once between the two mail servers and once between the sender and the sender's mail server.
- Simple mail transfer protocol employs commands and answers to transport messages between message transfer agents client and message transfer agents server.
- Message Transfer Agents, or MTAs, handle the actual mail transfer. To send mail from one system to another, the system needs both client and server message transfer agents.
Command:
MAIL FROM:<mail@abc.com?
5 . SNMP
- Simple Network Management Protocol, or SNMP, is a tool for gathering and organizing data from controlled devices on IP networks.
- Additionally, it alters the data to alter how the devices behave.
- The major purposes of SNMP are network management and monitoring.
- It comprises a collection of protocols for the application layer, a database schema, and a number of data items for network management.
Command:
snmpget -mALL -v1 -cpublic snmp_agent_Ip_address sysName.0
6 . DNS
- Domain Name System, or DNS for short, is a decentralized naming system for computers and other internet-connected devices that converts domain names of connected devices to numerical IP addresses and vice versa.
- The user does not need to memorize the domain's IP address thanks to DNS. Both the TCP and UDP protocols are supported by DNS.
- The port 53 is used by DNS servers. Generic domains designate registered hosts based on their generic behavior, country domains utilize a two-character country abbreviation, and inverse domains map addresses to maps.
- These three categories make up all domains.
Command:
ipconfig /flushdns
7 . DHCP
- Dynamic Host Configuration Protocol is known as DHCP.
- It is an application layer protocol for network administration.
- It enables the dynamic assignment of an Internet Protocol (IP) address to any device or network node so that they may interact using this IP.
- Assigning distinctive IP addresses to hosts is the primary objective of the DHCP protocol.
- Other network addresses, such as subnet mask, router address, vendor class identity, and DNS address, are provided in addition to unique IP addresses. A device can obtain a reliable network connection from a DHCP server using one of its pools of addresses.
Command:
clear ip dhcp binding {address | * }
8 . NFS
- A network file system is what it represents.
- It enables distant hosts to mount file systems over a network and use them just as they were locally mounted.
- System administrators can do this to concentrate resources onto centralized network servers. NFS's port number is 2049.
Command:
service nfs start
9 . X window
- It specifies a protocol for creating client/server programmes with graphical user interfaces. The goal is to enable a client—a program—to operate on a single machine.
- It is mainly utilized in mainframe networks that are linked together. For each server, the X window's port number rises by 1, starting at 6000.
Command:
Run xdm in runlevel 5
10 . LPD
- For Line Printer Daemon, it is an acronym.
- It is made to share printers.
- It is the component responsible for receiving and handling requests. An agent or server is a "daemon." LPD's port number is 515.
Command:
lpd [ -d ] [ -l ] [ -D DebugOutputFile]
Authors
- Samiksha Hiran
- Saurabh Jadhav
- Hrushabh Jadhav
- Aryan Jagadale


